CrowdStrike Outage Updates
,
Finance & Banking
,
Geo Focus: The United Kingdom
Regulator Tells Regulators to Enhance Third-Party Service Security
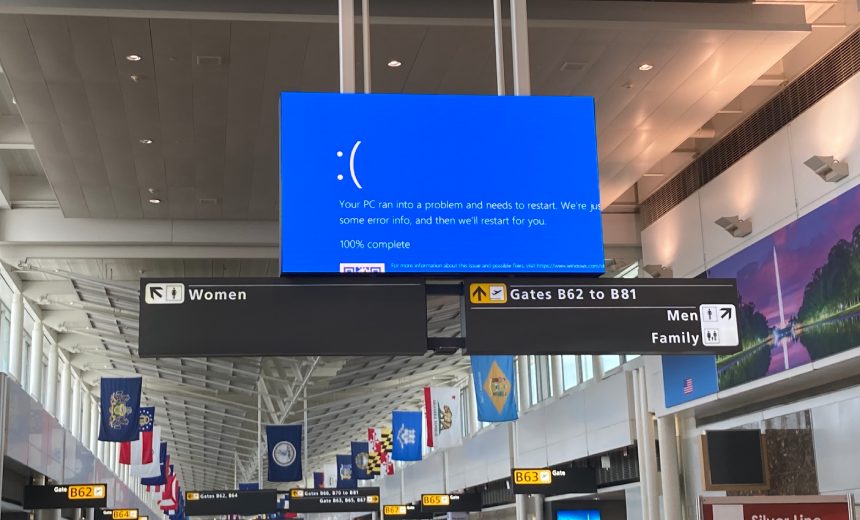
British financial institutions must ensure by this spring that they could reasonably weather a third party tech outage on the scale of July’s global meltdown of 8.5 million computers triggered by a faulty update from cybersecurity firm CrowdStrike.
See Also: Ransomware: Secure Backup is Your Last Line of Defense
The U.K. Financial Conduct Authority in Thursday guidance warned the financial sector it should be prepared to minimize the effects of a CrowdStrike-level event on consumers and markets. Issues with third parties constituted the leading cause of operational incidents reported to the FCA between 2022 and 2023.
Estimates of total direct losses caused by incident stand at stand at more than $5.4 billion as airlines grappled with canceled flights and several banks reported difficulties in processing transactions. Delta Air Lines is suing CrowdStrike to recoup what it said were $500 million worth of damages caused when CrowdStrike made an update to the Microsoft kernel (see: Delta Air Lines Sues CrowdStrike Over July System Meltdown).
The British agency said several organizations under its remit such as banks and insurers experienced “varying degrees of operational impact” from the outage, with minimal consumer harm. Financial firms that hewed to PS21/3 requirements for operational resilience of third-party services reported lesser impact in the wake of the July outage, the FCA said. Firms that had well-defined and tested communications strategies in place before the July outage were able to restore their systems relatively quicker with lesser impact.
“These outages emphasize firms’ increasing dependence on unregulated third parties to deliver important business services. This highlights the importance of firms continuing to become operationally resilient,” the regulator said.
To avoid potential large-scale fallout from similar incidents in the future, regulators urged firms to ensure compliance by March with the third-party service rule.
Financial organizations responding to a FSA inquiry stressed a need to identify single points of failure within their technology stack and said they are considering ways to ensure resilience including integrating systems with different operating systems.
They also recommended reviewing third-party management processes, contractual obligations, and system interdependencies to bring down the scale of any IT outage impact.
Concerns About Kernel Security
The CrowdStrike incident has brought about a global reevaluation of third party access to the Microsoft kernel, including by Microsoft itself (see: Kernel Mode Under the Microscope at Windows Security Summit).
Adam Meyers, Crowdstrike senior vice president, in September told the U.S. lawmakers that a “confluence of factors” were behind the outage. These include the company’s reliance on decade-old validation and testing processes that failed to detect the software glitch (see: CrowdStrike Blames ‘Confluence of Factors’ for Global Outage).
The German Federal Office for Information Security is leading discussions on developing software solutions that require minimum privileges.
Responding to a parliamentary inquiry, the U.K. government on Wednesday said permitting third-party software into the kernel is still necessary ” because not all operating systems provide non-kernel routes to get the data that third party security tools need for their analyses.”
“Vendors that have a genuine need to run code in the kernel have a responsibility for doing that in the lowest risk way that they can. This includes running thorough tests on new versions of that code, keeping the kernel code simple, and moving code out of the kernel that doesn’t need the full power, or justify the associated risk, that such access offers,” the U.K. government said.
