Endpoint Security
,
Hardware / Chip-level Security
,
Internet of Things Security
Cybersecurity Firm Warns of ‘Hidden Features’ in the Widely Used ESP32 Chip
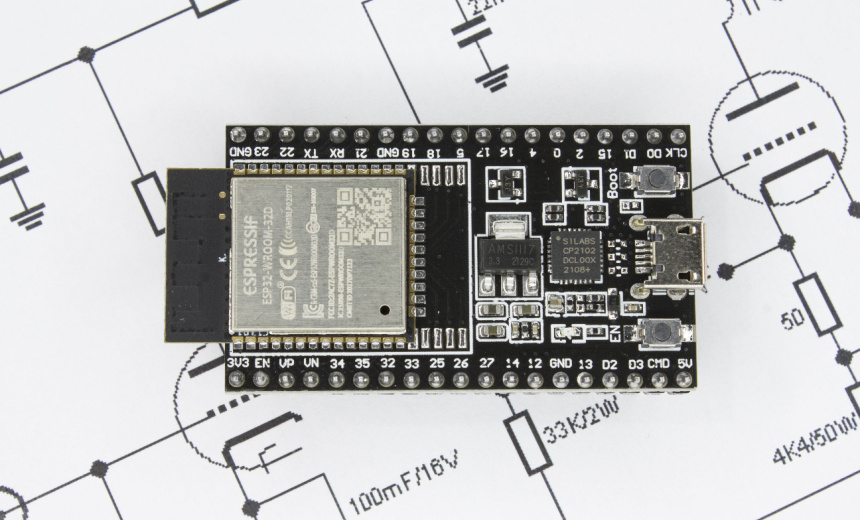
Low-cost, Chinese-made microcontrollers with integrated wireless networking could be manipulated into running malicious code due to a set of undocumented commands in the firmware, security researchers warn.
See Also: OnDemand | Protecting Devices and Software from Next-Generation Cyberthreats
The ESP32 microcontroller, manufactured by Shanghai-based Espressif Systems, retails for about $2 and up and includes WiFi and Bluetooth capabilities and a dual-core processor. The company says it’s sold more than 1 billion ESP32 units, which are built into many different types of mobile devices, wearable technology and IoT devices, including surveillance cameras. The chips are used in industrial IoT applications, including to build ESP32-based modules that plug into computers used for automation and monitoring and networking.
In a Thursday presentation at cybersecurity conference RootedCON in Madrid, two researchers from Spanish firm Tarlogic Innovation detailed what their organization billed as a “backdoor,” language the firm later revised as “hidden feature” after pushback that it oversold its research.
“We would like to clarify that it is more appropriate to refer to the presence of proprietary HCI commands, which allow operations such as reading and modifying memory in the ESP32 controller, as a ‘hidden feature’ rather than a ‘backdoor,'” the firm said in a statement.
Tarlogic researchers Miguel Tarascó Acuña and Antonio Vázquez Blanco reverse-engineered the ESP32 firmware – the vendor includes a copy of it on its GitHub page – and discovered 29 undocumented commands in the chip’s vendor-specific host controller interface, or HCI.
These can be used to write from the host to the controller in what might be an unexpected way. “These commands would allow modifying the chips arbitrarily to unlock additional functionalities, infecting these chips with malicious code and even carrying out attacks of identity theft of devices,” Tarlogic Innovation said.
“The use of these commands could facilitate supply chain attacks, the concealment of backdoors in the chipset or the execution of more sophisticated attacks,” it said. “Over the coming weeks, we will publish further technical details on this matter.”
In their presentation, researchers said the hidden command set could be used to change a device’s MAC address, which could be used to impersonate other devices. The commands can also inject packets into link management protocol traffic, potentially enabling an attacker to intercept traffic and directly control devices.
The hidden commands are now being tracked as CVE-2025-27840, assessed as posing a medium-severity risk.
Digital forensic expert Pascal Gujer said the hidden commands cannot be remotely exploited or exploited via an over-the-air attack, and that any attack would require wired access to the HCI as well as access privileges to the controller. “It’s a post-exploitation tool, not an instant game-over,” he said. “If an attacker already controls the host device, you’re cooked anyway.”
The ability for a manufacturer to add hidden or undocumented commands to their Bluetooth implementation is part of the specification itself. “The Bluetooth core specification lays out many HCI commands,” but also allows for vendor-specific commands, or VSCs, said cybersecurity researcher Xeno Kovah, co-founder of security consultancy Dark Mentor.
These VSCs “are commands that the silicon maker of the controller can use to manage the controller” and oftentimes get used for firmware updates as well as “to get back nice-to-have information that may not be available via spec-defined commands,” such as the temperature of the chip, or “how to perform chip-specific actions,” such as setting “a custom Bluetooth address,” he said.
Such commands can be used for debugging or during manufacturing, said security researcher Davi Ottenheimer.
Whether or not undocumented commands constitute a security vulnerability depends on the use case, including just how secure by design the device is meant to be for the specific way it’s being deployed, Dark Mentor’s Kovah said. Even so, “VSCs granting the capability to read and write memory, flash or registers” is “bad security design” and could compromise attempts to use features such as secure boot that are built into Espressif’s chip, although disabled by default, he said.
