Business Continuity Management / Disaster Recovery
,
Cryptocurrency Fraud
,
Fraud Management & Cybercrime
Alpha Wellness Says ‘Devastating’ Incident Forced Closure of Georgia-Based Center
Another small medical care provider has shut its doors forever as the result of a recent “devastating” cyberattack and data theft.
See Also: On Demand | From Patch to Prevention: Modernizing Remediation Across Hybrid Environments
Georgia-based Ascension Health Services LLC – which did business as Alpha Wellness & Alpha Medical Centre – decided to permanently pull the plug on its operations in April following an attack allegedly carried out by cybercriminal gang RansomHub, which lists the practices as a victim on its darkweb site.
Alpha Medical Centre and Wellness on July 8 reported to the U.S. Department of Health and Human Services a HIPAA breach involving a hacking/IT incident on a network server, which affected 1,714 individuals.
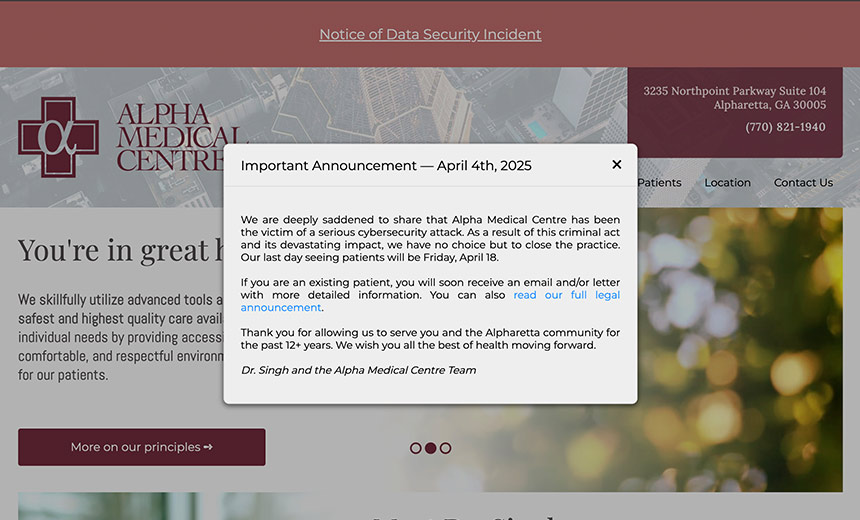
“We are deeply saddened to share that Alpha Medical Centre has been the victim of a serious cybersecurity attack,” the practice said in a notice posted on its website. “As a result of this criminal act and its devastating impact, we have no choice but to close the practice.” Alpha’s last day of seeing patients was April 18.
While it’s unclear how many patients 12-year-old Alpha Medical Centre and Wellness had before closing up the practice, the organization’s reported breach is small relative to the many other protected health information compromises that get posted every day to the HHS’ Office for Civil Rights’ HIPAA Breach Reporting Tool website listing breaches affecting 500 or more individuals.
Alpha Medical Centre’s sister organization, Alpha Wellness, which operated out of the same office, was led by the same physician, Dr. Rajender Singh, and offered an “array of holistic and wellness services” – has a similar message posted on its website.
Although Alpha’s legal name is Ascension Health Services LLC, it is not affiliated with the much larger, Catholic healthcare organization Ascension, which operates hospitals and other facilities in 16 states, an Ascension spokesman told Information Security Media Group.
Alpha Medical Centre and Wellness did not immediately respond to ISMG requests for additional details about the cyberattack and the reasons for permanently closing the practices.
A longer breach notice also posted on both of Alpha’s websites said that on Feb. 3, the organization “fell victim to a cyberattack.”
The investigation into the incident determined that an “unauthorized party” may have accessed or acquired certain patient personal information, including individual names, address, email address, phone number, health insurance information and medical appointment details. “Not all data elements were impacted for every individual.”
To date, the entity said it is not aware of any identity theft or financial fraud as a result of the incident.
Other Closures
Alpha Medical Centre and Wellness join a list of other smaller healthcare entities that have gone out of business in recent months and years following cyberattacks on their organizations.
Pinehurst Radiology, a small North Carolina radiology practice shut down its operations earlier this year following a January cyber incident (see: Radiology Clinic, Hospital Among Latest Rural Cyber Victims).
The radiology group reported a hacking incident to HHS OCR in March that affected 8,600 people. An operator at FirstHealth of the Carolinas, which operates several North Carolina hospitals, told ISMG on Tuesday that Pinehurst Radiology shut down permanently around June after being at least temporarily closed immediately following the January attack.
A notice on Pinehurst Radiology’s website about the data breach instructs patients how to obtain their various Pinehurst Radiology medical imaging records, including directing patients to FirstHealth for help accessing mammography records.
Several other smaller healthcare organizations have also closed in recent years after being unable to fully bounce back from the technological and financial blow of a cyberattack.
That was the case for a 44-bed hospital operated by St. Margaret’s Health in Spring Valley, Illinois, which permanently closed its doors in 2023 in part due to a 2021 ransomware attack that worsened financial woes and other problems that it was already dealing with before the incident (see: Rural Healthcare Provider Closing Due in Part to Attack Woes).
Wood Ranch Medical, a small clinic in Simi Valley, California, in 2019 also announced it would close for good after being unable to recover access to any of its records as a result of a ransomware attack (see: Latest US Healthcare Ransomware Attacks Have Harsh Impact).
Ransomware attacks can be especially devastating for smaller healthcare organizations because of a combination of financial, operational and regulatory issues, said Tamra Durfee, virtual CISO at Fortified Health Security.
These post-breach burdens include the high recovery costs of a ransomware event and inadequate cyber insurance coverage to cover losses; operational disruption as a result of the loss of access to patient records and the manual recovery of these records being slow or incomplete and regulatory consequences resulting in mandatory reporting and potential fines, she said.
“Even when small healthcare entities manage to reopen after a ransomware attack, many continue to struggle significantly, both financially and operationally,” she said.
To help avoid a fate similar to Alpha Medical Centre and other firms that have closed in the wake of damaging cyberattacks, healthcare organizations should consider taking several critical steps in advance, she said.
“Ensure adequate cyber insurance. Recovery costs can be overwhelming without financial support. Review your cyber liability insurance to ensure it covers ransomware, data restoration, legal fees and business interruption. Understand policy exclusions and response timelines,” she stressed.
“Also, learn from others and share threat intelligence. Alpha Medical Centre’s experience is not unique. Join healthcare information sharing and analysis centers or local cybersecurity coalitions to stay informed. Participate in peer learning and threat-sharing networks,” she said.
