Fraud Management & Cybercrime
,
Social Engineering
Users Download Malware in Bid to Placate Meta
A newly surfaced FileFix social engineering campaign puts a new spin on ClickFix attacks by goading users into loading malware under the guise of reporting a wrongful account suspension to social media giant Facebook.
See Also: Live Webinar | AI-Powered Defense Against AI-Driven Threats
ClickFix attacks have surged over the last year as a technique for manipulating users into executing malicious code by offering supposed steps to fixing a technical problem. A hacker going by “mr. d0x” in June demonstrated a stealthier version that shifts the focus of the social engineering prompt away from the Windows Run dialog window to the more familiar Windows File Explorer.
Researchers from backup and recovery firm Acronis said Tuesday they discovered “a rare in-the-wild example” of a FileFix campaign. “The adversary behind this attack demonstrated significant investment in tradecraft,” making it more sophisticated than ClickFix attacks.
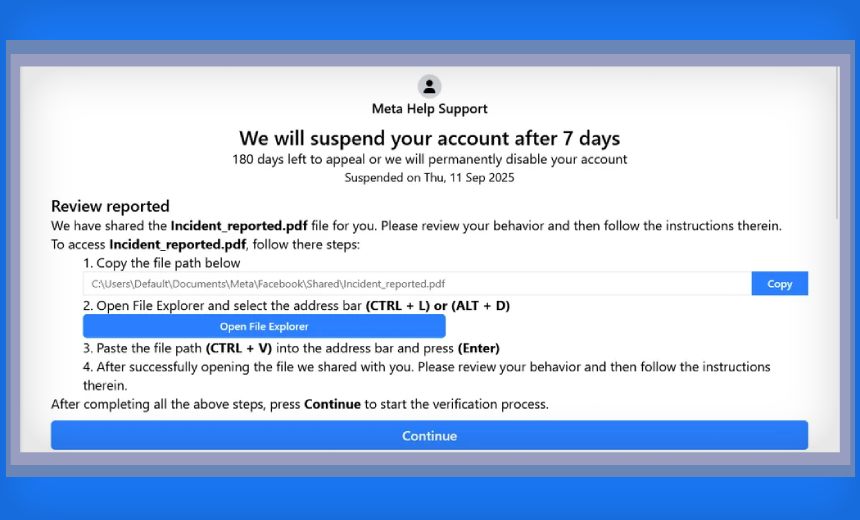
Victims likely get sucked into the scam by following a link from a phishing email. The link leads to a message from “Meta Help Support” warning that Facebook will suspend a user’s account and delete it after 180 days, unless the victim files an appeal.
The website reached by the phishing email prompts the user to open File Explorer to supposedly view a PDF file shared by Facebook. “But, alas, the ‘File Explorer’ that they opened is a file upload window, and the path that they’d pasted into its address bar is a payload,” Acronis wrote. Hackers hide the malicious commands transmitted to Windows in the supposed file path with “a lot of spaces.”
Users then see an alert that “No file is found” and can continue to another page, ordering them to “Please complete the steps.” By then, a malicious payload in the background is already executing a PowerShell script. Unusually, the script downloads an image – but the image contains a steganographic payload. Once downloaded, those images are parsed to extract and execute hidden code.
That first stage decrypts and decompresses additional payloads. Some are DLLs and executables, often run through conhost.exe before being deleted to cover tracks. The campaign launches a loader written in Go. It performs sandbox checks to avoid analysis, encrypts strings to frustrate researchers and finally drops StealC, an infostealer capable of raiding browser credentials, crypto wallets, messaging apps and cloud services.
StealC is among the top advertised infostealers on darkweb forums, alongside Lumma, RisePro, Vidar and RedLine based on stealer log activity. StealC has evolved quickly from earlier infostealer variants, and the latest build has faster command and control and stronger obfuscation and expanded data-theft features like multi-monitor screenshots and a unified file grabber.
The campaign uses phishing lures translated into different languages and obfuscation methods change from sample to sample. Indicators of compromise tie activity to the United States, Germany, China, Bangladesh, Tunisia, Nepal, the Philippines, Serbia, Peru and the Dominican Republic, among other countries. The breadth suggests opportunistic rather than precision targeting.
