Attacks on RMM Tools Surged in 2025, With 51 Solutions Flagged as Targets

Remote monitoring and management, or RMM, tools gained traction during the COVID era when work from home was a mandate. But RMM tools are now being weaponized by cybercriminals. Once adversaries gain remote access using tools, such as SuperOps and TeamViewer, they can disable scheduled backups, destroy images and restore points and push ransomware to thousands of endpoints.
See Also: Identity and Access Management (IAM) Market Guide 2025
RMM tools are used by IT professionals and managed service providers to remotely monitor, manage and maintain client IT systems via a centralized dashboard. Threat actors access these tools with authenticated credentials to avoid triggering security alerts and alarms. It’s comparable to sharing one’s RFID access card to enter their home or office.
Why RMM Tools Are Targeted
Legitimacy mask threat: RMM tools are deeply embedded in enterprise IT workflows and their traffic patterns often bypass anomaly detection due to their perceived legitimacy, creating a persistent blind spot in network monitoring;- Privileged access as an attack vector: RMM platforms typically operate with elevated permissions across endpoints. Once compromised, they offer adversaries a ready-made channel for privilege escalation, lateral movement and payload delivery, including ransomware;
- MSP compromise via supply chain: Targeting an MSP’s RMM infrastructure enables adversaries to pivot into multiple client environments simultaneously. This supply chain exposure significantly amplifies the blast radius and monetization potential of a single intrusion;
- Tool mimicry and credential abuse: Threat actors frequently repurpose legitimate RMM tools or hijack valid credentials, allowing malicious activity to blend seamlessly with routine administrative tasks. This tactic complicates detection and response, especially in environments lacking behavioral baselining.
Exploitation Routes
The Acronis Cyberthreats Report, H1 2025,
identifies RMM attacks as a significant threat vector. The report says the trend accelerated in 2025, with more than 51 RMM solutions identified as potential attack vectors. Some tools are more frequently targeted than others, for example, Splashtop, ConnectWise, ScreenConnect and Atera have been repeatedly abused in real-world intrusions, according to the Acronis Threat Research Unit, or TRU.
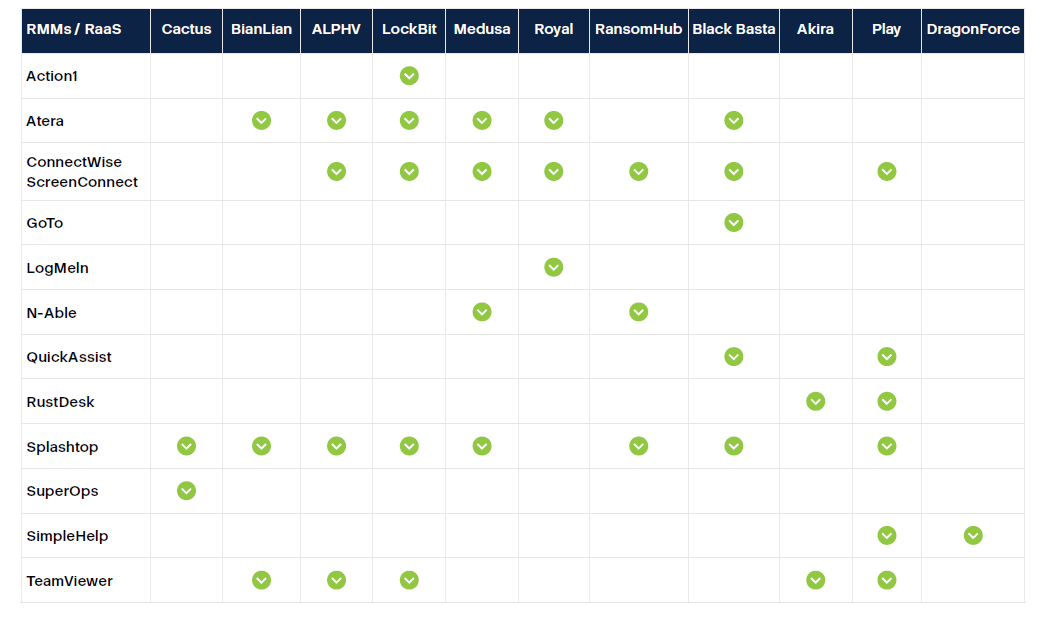
Adversaries take several approaches to exploit RMM tools and their privileged access:
- Exploiting vulnerabilities in RMM software to gain unauthorized access;
- Compromising an RMM user’s credentials, often through phishing or brute-force attacks;
- Tricking an employee into downloading a malicious RMM installer via phishing emails or fake software updates;
- Using the RMM tool’s native features to deploy malicious payloads and exfiltrate data, making the activity appear legitimate.
Hunters International Hack
In 2024, a manufacturing firm in the U.K. was targeted by a cybercriminal group called Hunters International. The group used legitimate RMM tools, including ScreenConnect, to sustain covert access to the company’s network for over a month.
The attackers strategically used a mix of the exploit methods to bypass conventional security defenses, ultimately culminating in the deployment of ransomware.
First, they used phishing-delivered installers or trojanized update packages to deploy legitimate RMM tools. These tools, trusted by IT environments, allowed attackers to bypass endpoint detection systems by masquerading as routine administrative activity.
Once installed, the attackers gained persistent access, moved laterally across networks and staged data for exfiltration.
Ransomware payloads were often delayed, allowing stealthy reconnaissance and data theft before encryption.
The compromised RMM tools enabled remote execution, script deployment and encrypted peer-to-peer connections, thereby complicating detection.
CISO’s Viewpoint
Sunil Varkey, a veteran CISO who is now a security and artificial intelligence evangelist, told Information Security Media Group that attacks involving RMM exploitation will have a high success rate as it is a trusted software service.
“This is a typical living-off-the-land attack used by many adversaries considering the success and ease of execution. Typically, such software are whitelisted in most of the controls to avoid blocking and noise, due to which its activities are not monitored much,” Varkey said. “Like in most adversarial acts, getting access to the software is their initial step, so if access is limited to specific people with multi-factor authorization and audited periodically, unauthorized access can be limited. If the baseline of existing good RMMs activities, originator and patterns can be mapped, any deviation that can be identified sooner.”
Gerald Beuchelt, CISO at Acronis, advised CTOs and CISOs to reallocate their budget from “shiny” new technology to hardening existing tools, as it’s far cheaper than paying ransoms. “In my experience, organizations that treat RMM as a ‘set-it-and-forget-it’ utility may end up paying dearly later.”
“Treat RMM seriously. Assume compromise is possible and build defenses around prevention, detection and rapid response. Start with a full audit of your RMM deployment – map every agent, session and integration to identify shadow access points: asset management is key and a good RMM solution should be able to assist here. Layered controls are key – think defense-in-depth tailored to RMM’s remote nature,” Beuchelt said.
Prevention and Risk Mitigation
Since ransomware gangs use social engineering techniques and hyper-realistic phishing using generative artificial intelligence, end users and enterprises are advised to follow these measures.
User Practices
- Refrain from opening suspicious emails or running unknown files;
- Use strong passwords and rotate them regularly;
- Enable multifactor authentication and enforce session timeouts under 15 minutes;
- Conduct user awareness training and phishing drills.
Access Controls
- Enforce least-privilege access with PAM solutions granting just-in-time, just-enough permissions;
- Configure VPN jump hosts with unique credentials;
- Restrict access by IP, host, or VLAN instead of broad network access.
System and Endpoint Security
- Keep systems and software updated;
- Use antivirus or endpoint agents to monitor traffic;
- Whitelist only approved RMM executables, disable unverified auto-updates and deploy EDR agents tuned for suspicious activity.
Monitoring and Response
- Integrate RMM into the incident response playbook and simulate attacks through purple team exercises;
- Move beyond signature-based alerts toward behavioral baselining;
- Integrate SIEM with RMM logs for anomaly detection.
Vendor and Supply Chain Security
- Perform regular configuration scans and enforce supply chain security measures;
- Validate SOC2 Type II and ISO 27001 audits regularly;
- Use continuous vendor monitoring tools, such as SecurityScorecard and Bitsight, noting limitations in data freshness.
