Cyberwarfare / Nation-State Attacks
,
Fraud Management & Cybercrime
US Critical Infrastructure, NATO Also Targeted by Russian Threat Actors, Feds Say
More than two years after Moscow launched an unprovoked war of conquest against Ukraine, U.S. federal prosecutors charged a Russian man with facilitating wiper malware used to support the invasion.
See Also: Webinar | Everything You Can Do to Fight Social Engineering and Phishing
The U.S. Department of Justice on Wednesday accused Russian civilian Amin Stigal of aiding his country’s military in its use of WhisperGate wiper malware disguised as ransomware to destroy Ukrainian government and civilian systems. Targets during a digital campaign, which the Kremlin launched a month before Russia’s all-out invasion in February 2022, included critical infrastructure. The aim was to “sow concern” among the Ukrainian populace, prosecutors said.
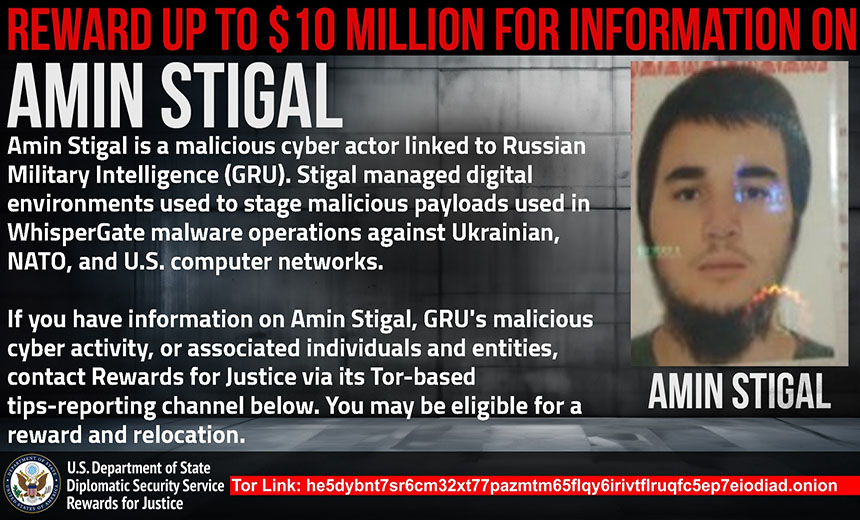
An indictment unsealed Wednesday charges Stigal with participating in a conspiracy to commit computer intrusion and cause damage in support of the foreign intelligence branch of the general staff of Russia’s military, referred to as the GRU.
“Conspirators hacked the computers of dozens of Ukrainian government entities, including in critical infrastructure, as well as entities responsible for other sectors with no military or defense-related roles, including agriculture, education and science, and emergency services, and destroyed or attempted to destroy those systems in advance of the Russian invasion,” the indictment says.
Prosecutors say Stigal also supported the GRU’s hacking of an unnamed Central European country that supported Ukraine with civilian and military aid. He allegedly probed U.S. critical infrastructure, “including multiple sites maintained by a U.S. government agency located in Maryland.”
Attackers attempted to disguise their identity, in part by launching attacks using infrastructure located abroad, paid for in cryptocurrency.
The U.S. Department of State Rewards for Justice Program posted a reward for information on Stigal or the GRU’s “malicious cyber activity or associated individuals and entities.” In addition to a monetary reward, informants could be eligible for relocation.
The government’s description of Stigal as a “malicious cyber actor” doesn’t make clear if he was employed as an IT administrator or offensive hacker by the GRU. “As early as 2021, digital environments managed by Amin Stigal were used to stage malicious payloads used in various WhisperGate malware campaigns,” the government said. “Stigal is linked to WhisperGate operations against Ukrainian, NATO and U.S. computer networks and has conspired with others to establish accounts on a social communications platform for use in WhisperGate operations.”
Security researchers previously tied the group behind WhisperGate to a Telegram channel with the handle Free Civilian, which connected to a dark web hack-and-leak site of the same name.
Microsoft in mid-2023 attributed the WhisperGate attacks to a GRU-affiliated threat actor with the codename Cadet Blizzard, which it said became operational by 2020. The group is distinct from other well-known Russian military intelligence hacking groups such as Sandworm and APT28, which is also known as Fancy Bear, the technology giant said.
WhisperGate was designed for noisy attacks – it deletes the Windows master boot record, leaving systems unable to start up, Microsoft said.
Wiper Malware’s Rise and Fall
WhisperGate is one of over a dozen different types of wiper malware deployed during the ongoing war. On the day Russia launched its all-out invasion, the GRU wiper attacks affected 300 systems across a dozen government and command-and-control organizations, Chad Sweet, CEO of consultancy The Chertoff Group, said in a mid-2022 interview (see: Major Takeaways: Cyber Operations During Russia-Ukraine War).
Russia also unleashed AcidRain malware, a wiper that permanently disabled tens of thousands of Viasat KA-SAT satellite communications network consumer broadband modems.
Russia’s deployment of wiper malware led to wait times of up to 40 hours at the Ukraine-Poland border as women and children attempted to flee the start of the conflict, said Mikko Hypponen, chief research officer at WithSecure, in a mid-2022 interview.
“They couldn’t leave and people were stumped – like, ‘Why are the borders closed?'” he said. “The borders weren’t closed, but the computers of the Ukraine border control had been wiped by HermeticWiper, which was developed and deployed by the GRU from Russian military intelligence. That’s what cyberwar looks like in the real world.”
By mid-2022, cybersecurity firm Trellix reported seeing at least 15 distinct wipers being used by Russian forces during the conflict, including AcidRain and WhisperGate.
While the tempo of wiper malware operations remained furious in the immediate pre- and post-invasion periods, security experts said Russia eventually appeared to have burned through its arsenal – potentially because Moscow’s military planners anticipated a quick victory. Subsequently, the GRU and other Russian hacking teams appear to have shifted their focus to cyberespionage and cyber operations to support the stalled ground offensive.
