Fraud Management & Cybercrime
,
Social Engineering
Chinese-Speaking Operators Have Made Lucid a ‘Primary Source’ of Phishing
Security researchers say they expect a surge this year in text message smishing fueled by a phishing-as-a-service platform operated by Chinese-speaking threat actors.
See Also: Live Webinar | AI-Powered Defense Against AI-Driven Threats
The platform, called Lucid, enables large-scale smishing campaigns active in 88 countries. The platform allows attackers to deliver malicious links to Apple iMessage and Android’s Rich Communication Services. It offers a built-in credit card generator for one-stop-shop validation by hackers of stolen payment data.
Lucid already is a primary source of phishing campaigns targeting users in Europe, the United Kingdom and the United States. “Initially operating at a local level, its impact has grown substantially, with a significant surge expected by early 2025,” warn researchers at threat intel firm Catalyst.
Lucid operates on a subscription-based model, allowing cybercriminals to launch automated and customizable phishing attacks. The service includes advanced anti-detection mechanisms such as IP blocking and user-agent filtering, prolonging the lifespan of phishing sites.
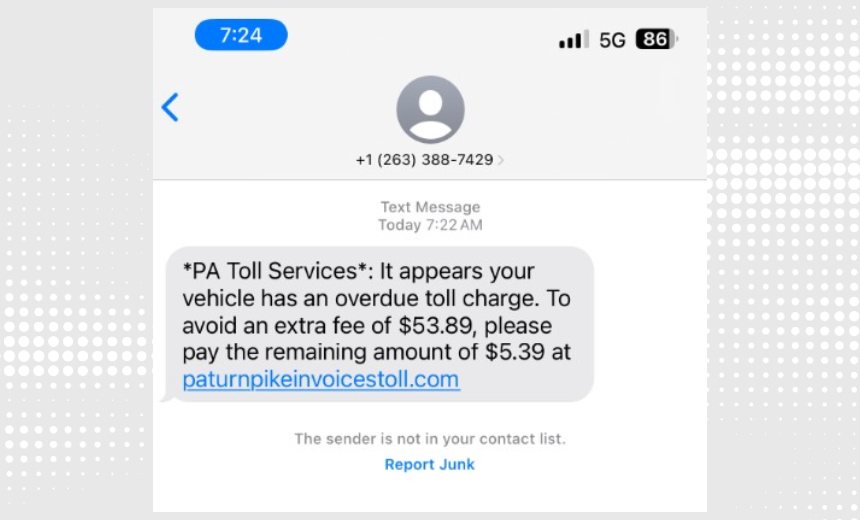
The group behind Lucid, also known as “Black Technology” or “XinXin,” has been active since 2023. The service is primarily used to steal credit card details and personally identifiable information through texts that masquerade as originating from legitimate organizations such as postal services, courier companies and government agencies. In the U.S., users have reported a surge over the past year of smishing texts purporting to come from a road toll collection service. The FBI published a warning about the scam in 2024. Consumers apparently continue to be hoodwinked, causing the U.S. Federal Trade Commission to warn about it in January, the Colorado state government to alert drivers earlier this year and the attorney general of Vermont to post in March a scam warning.
Catalyst wrote that operational data indicated that Lucid-driven campaigns have an average success rate of approximately 5%.
Lucid operates over the internet rather than through telecom networks. This approach increases message delivery rates and also enables attackers to evade telecom filtering mechanisms. Lucid also employs obfuscation techniques, such as time-limited URLs and device fingerprinting, to evade detection by security analysts and automated threat intelligence systems.
Its phishing pages are tailored to victims’ locations, mimicking the websites of local organizations to appear more convincing. The service also exploits automation tools that allow attackers to create and deploy phishing campaigns with minimal effort.
Lucid provides a structured attack infrastructure. Threat actors acquire phone numbers through data breaches, open-source intelligence gathering and underground marketplaces.
The platform is one of several PhaaS platforms alongside services such as Darcula and Lighthouse (see: Phishing-as-a-Service Platform Offers Cut-Rate Prices).
The group behind Lucid actively markets its services on Telegram, where it advertises their ability to send over 100,000 smishing messages daily. Lucid appears to operate on a hierarchical structure, supporting multiple roles, including administrators, employees and guest users. Licenses for the platform are sold on a weekly basis, with automatic suspension if not renewed.
