Endpoint Security
,
Governance & Risk Management
,
Healthcare
The Next Major Cyber Risk Could Come Through a Biological Sample

A new class of cyberthreat is emerging – one that bypasses firewalls and evades endpoint security. Instead, it enters organizations through biological samples.
See Also: Going Beyond the Copilot Pilot – A CISO’s Perspective
In my years in cybersecurity, I have witnessed threat vectors evolve far beyond what we once thought possible. We defended networks, endpoints and cloud stacks. Now we must look at living systems. Researchers at the University of Washington demonstrated that it is feasible to encode executable payloads into synthetic DNA that, once sequenced and processed, could trigger malware in sequencing software. This convergence of biology and cyberthreats is not science fiction. It is real and demands urgent attention globally.
Why DNA Malware Matters for Business
DNA is an information medium. When sequencers convert biological samples into digital data, that information flows through bioinformatics pipelines, cloud services and human-written software. If an adversary designs a DNA sequence with hidden instructions, that malware can exploit vulnerabilities in sequencing software to achieve remote code execution or data corruption.
A Nature study, among other scientific reports, confirmed the theoretical and practical viability of this threat vector. For Australia’s expanding genomic research sector, biotech firms, health tech startups and agricultural genomics operations, the implications are significant and could affect:
- The integrity of national health and genomic datasets;
- Protection of intellectual property and R&D pipelines;
- Agritech biosecurity and high-value export markets;
- Regulatory and reputational risk across the life sciences supply chain.
Anatomy of the Attack
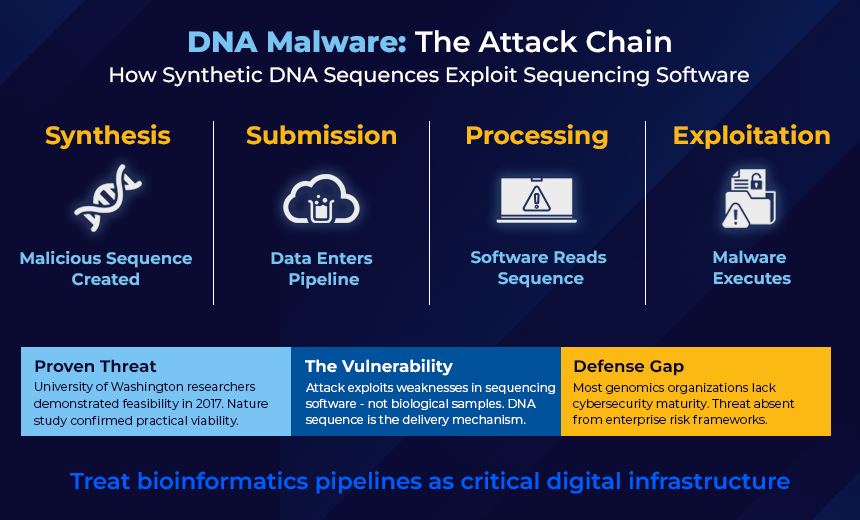
How could it happen? An attacker synthesizes a DNA sample with encoded malicious payload – for example, a compressed exploit or a call to a specific IP address. The sample is submitted for sequencing, possibly through a third-party lab, and processed through a standard bioinformatics pipeline. The sequenced output triggers code in downstream software, exploiting vulnerabilities such as buffer overflows or unsafe parsing to execute malicious commands.
The attacker gains control or corrupts analysis, altering results in genetics, diagnostics or biotech production. Traditional cyber controls fail to detect the threat because biochemical input or DNA is encoded as data and not conventional digital vectors.
Australia’s Exposure and Opportunity
Australia’s genomic research institutions, medical laboratories, biotech startups and agricultural genomics operations depend on sequencing and analysis pipelines that are increasingly connected to cloud-first environments. Yet, cybersecurity maturity in this domain is low.
Biotechnology organizations conduct threat modeling or penetration testing equivalent to traditional IT systems. Globally, the concept of “DNA malware” gained attention after the University of Washington’s 2017 proof of concept, but it is absent from most enterprise cyber risk frameworks, vendor assessments and regulatory guidance.
For Australia, the challenge is twofold: the country is a target as a biotechnology innovator as well as a systemic vulnerability as a nation reliant on genomic data.
What Organizations Can Do
The bioinformatics supply chain and sequencing ecosystem must now be treated as critical digital infrastructure. To mitigate this emerging threat, certain measures are essential:
- Secure sample intake and provenance: Labs must verify sample origins, treat all DNA as untrusted until validated and log the chain of custody.
- Strengthen software hygiene in sequencing pipelines: Code that processes sequenced DNA must adopt secure development practices such as input validation, memory safety and fuzzing.
- Apply encryption and integrity verification across all sequencing data: From the physical sample to raw data and analytical results, authenticity must be protected.
- Conduct threat modeling for synthetic biology and genomics: Maliciously crafted DNA must be included as a scenario in risk assessments.
- Encourage cross-disciplinary collaboration: Establish cyber-biotechnology/bioinformatics working groups across IT, R&D, lab operations and compliance. Align with global frameworks and advocate for national cyber-biosecurity standards.
Takeaways for Cybersecurity Professionals
- Add genomic pipelines to your risk landscape: If your organization depends on DNA sequencing, treat the entire workflow as a potential attack vector.
- Vet your vendors: The lab, sequencer manufacturer and software provider each represent exploitable links.
- Run adversarial simulations: Model scenarios involving malicious DNA samples and test containment and response.
- Invest in audit and visibility: Demand proof of vulnerability assessments and code reviews in bioinformatics software.
- Engage at a policy level: Promote the recognition of cyber-biosecurity as a formal risk category and advocate for industry standards and reporting mechanisms.
The genome is no longer just a blueprint for life; it is a new battlefield for code. When a vulnerability in a sequencer becomes a vulnerability in national health or food security, the stakes are existential.
Australia has the opportunity to lead globally in this frontier, but only if it recognizes that biology and cyber are now inseparable and prepares accordingly.
The first DNA-borne malware may not come from a hacker, but from a careless lab, an unpatched sequencer or an insecure pipeline. The question is not if, but when. And those who understand this threat now will help define resilience for the next decade.
