Leadership & Executive Communication
,
Training & Security Leadership
Apply These Proven Methodologies to Assess, Prioritize and Act Quickly in a Crisis

We hear a great deal about the need for soft skills in cybersecurity – things like communication, team building and critical thinking. But all too often, we don’t place enough emphasis on applying practical strategies to help get the work done. Cybersecurity professionals frequently deal with multiple issues – all demanding immediate attention.
See Also: Gartner Report | Break Free From Security Complexity. Platformization Delivers Simplicity.
How can you demonstrate the ability to make sound decisions to advance your career? Decision-making in high-stakes environments demands clear methodologies that promote both efficiency and accuracy. Here’s a high-level overview of four different decision making approaches you can use when faced with critical choices.
OODA Loop
The OODA Loop, attributed to military strategist John Boyd, guides users through a four-step cycle: Observe, Orient, Decide and Act. The loop was designed for combat pilots to make decisions very quickly. Observe all input, orient to the surroundings using previously learned and synthesized information, decide, act and quickly reiterate the loop.
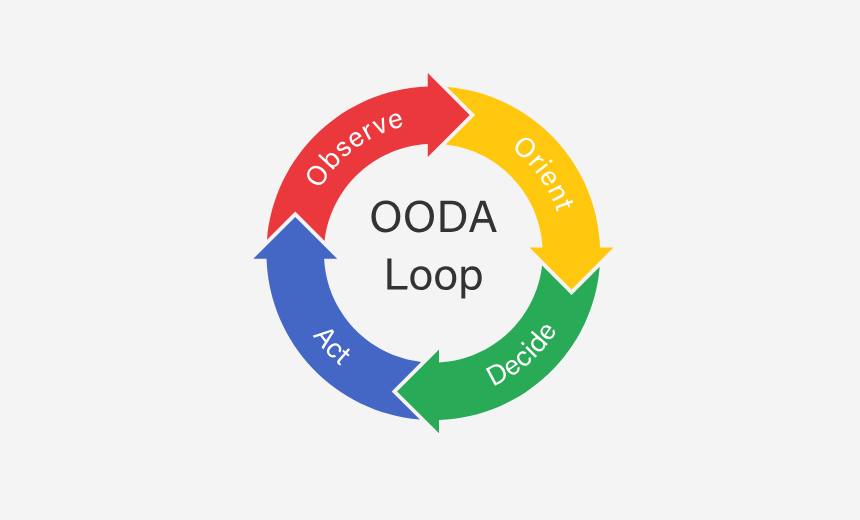
Security teams can apply the OODA Loop when rapid incident evaluation is necessary, particularly during live threats that call for iterative updates. This method requires minimal overhead. It is a rapid, continuous cycle of observing, orienting, deciding and acting. Incident responders often use OODA when minutes count and any delay could exacerbate damage. Learn more about how the OODA framework can be used in cybersecurity operations to combat nation-state threats.
Eisenhower Matrix
The Eisenhower Matrix highlights the distinction between urgency and importance, thereby preventing high-value tasks from being overshadowed by more immediate but less strategic concerns. It was developed as a time management strategy with the idea that proper planning can help prevent items from reaching critical, red-light flashing emergencies.
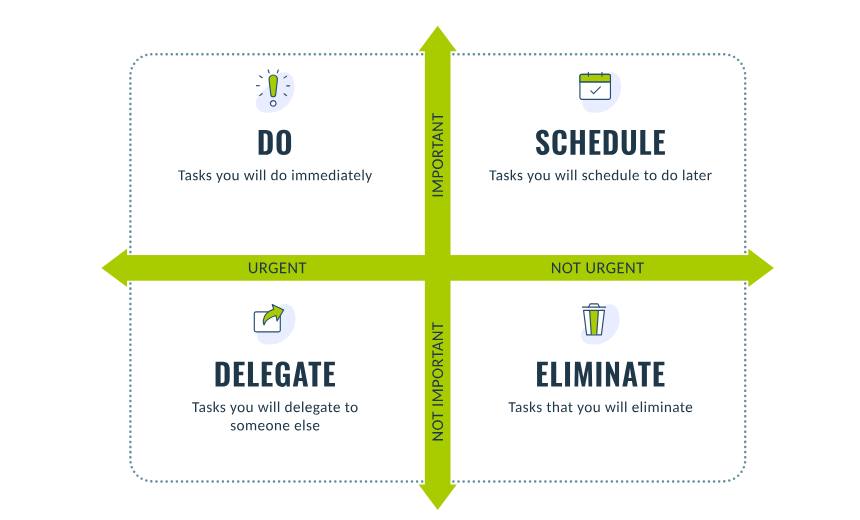
The Eisenhower Matrix works by creating a four-square grid with “urgent” and “not urgent” on one axis and “important” and “not important” on the other. Security teams can use this matrix to prioritize and schedule things such as vulnerability remediation along with longer-term initiatives such as employee training and policy reviews. Managers can list their tasks and place them in the appropriate quadrant, deciding which to tackle immediately, schedule for later, delegate to others, or eliminate.
This matrix requires less data analysis compared to a risk matrix, and it can be done quickly with a whiteboard or a shared spreadsheet. Cybersecurity teams and IT service management teams use it for triage when resources are stretched thin.
Risk Matrix
A risk matrix framework plots potential threats or vulnerabilities according to their likelihood of occurrence and their potential impact. As the situation increases in complexity, additional rows and columns can be added with definitions to help determine where to place risk factors. For example, a “severe” impact rating could be defined as “businesses operations down for greater than one hour.”
This approach helps decision-makers focus on the most significant risks, with those that are severe and probable handled first. The risk matrix can be completed relatively quickly if the team already has up-to-date risk data. It may demand more collective input and historical data than the Eisenhower Matrix, particularly if the threat environment is complex. Cybersecurity professionals frequently use risk matrices during planning cycles to allocate budgets and personnel according to well-defined priorities.
NIST Risk Management Framework
The National Institute of Standards and Technology Risk Management Framework supports a lifecycle methodology for categorizing systems, selecting and implementing security controls, assessing those controls, authorizing operation and maintaining continuous monitoring.
This iterative framework applies particularly well in compliance-bound environments such as healthcare, financial services and government. Practitioners who deploy the NIST RMF engage in a standardized sequence that ties security decisions to documented risk thresholds. NIST RMF requires considerable time, planning and documentation to implement correctly. Organizations that adopt this framework typically have a regulatory or policy-driven need for rigorous oversight. Expanded guidance can be found in NIST Special Publication 800-37.
These frameworks serve as valuable assets for cybersecurity professionals faced with addressing multiple issues under tight time constraints. Each model provides a systematic lens for understanding and managing complex tasks that affect organizational security.
The underlying principles of good decision-making transfer to other areas of professional development because clear prioritization are valued in any industry that demands high accountability. Adopting and refining these tools can differentiate a candidate in the job market by showcasing both technical competence and strategic thinking. Organizations that integrate such methodologies into daily operations can benefit from improved efficiency, reduced oversight and a measured approach to risk.
