Identity & Access Management
,
Security Operations
‘Don’t Panic,’ Say Developers

Security researchers identified an attack method against a commonly used network authentication protocol that dates back the dial-up internet and relies on an obsolete hashing function.
See Also: Access Management Alone is Not Enough: Unified Identity Security Approach
The attack scenario – researchers say a “a well-resourced attacker” could make it practical – fools the Remote Authentication Dial-In User Service into granting access to a malicious user without the attacker having to know or guess a login password. Despite its 1990s heritage and reliance on the MD5 hashing algorithm, many large enterprises still use the RADIUS protocol for authentication to the VPN or Wi-Fi network. It’s also “universally supported as an access control method for routers, switches and other network infrastructure,” researchers said in a paper published Tuesday. The protocol is used to safeguard industrial control systems and 5G cellular networks. Authors include academics at the University of California-San Diego and researchers with Cloudflare, BastionZero, Microsoft and Centrum Wiskunde & Informatica.
“RADIUS appears to have received notably little security analysis given its ubiquity in modern networks,” the researchers said.
Dubbed Blast-RADIUS, the man-in-the-middle attack spoofs a RADIUS client into granting access to a hacker despite the RADIUS server rejecting the request. The vulnerability is tracked as CVE-2024-3596.
Having the ability to intercept and modify RADIUS traffic means the attacker must have already hacked into a network – or is able to intercept protocol traffic sent over the open internet, despite advice against doing so. “Even if RADIUS traffic is confined to a protected part of an internal network, configuration or routing mistakes might unintentionally expose this traffic,” the researchers said. They also said that relying on network separation as a security protection goes against the federal government’s concept of zero trust architecture, which says that “no network is implicitly considered trusted.”
The attack must originate, or appear to originate, from a known client of the RADIUS server, Cloudflare said. But apart from that condition, RADIUS access request messages typically don’t include authentication or integrity checks, making them vulnerability to man-in-the-middle attacks.
The crux of the vulnerability is a MD5 collision attack conducted by the attacker to forge an Access-Accept response from the RADIUS server, which the attacker passes to the RADIUS client, which authenticates the malicious user. Because the attack forges the authentication message, implementing multifactor authentication wouldn’t be an effective mitigation.
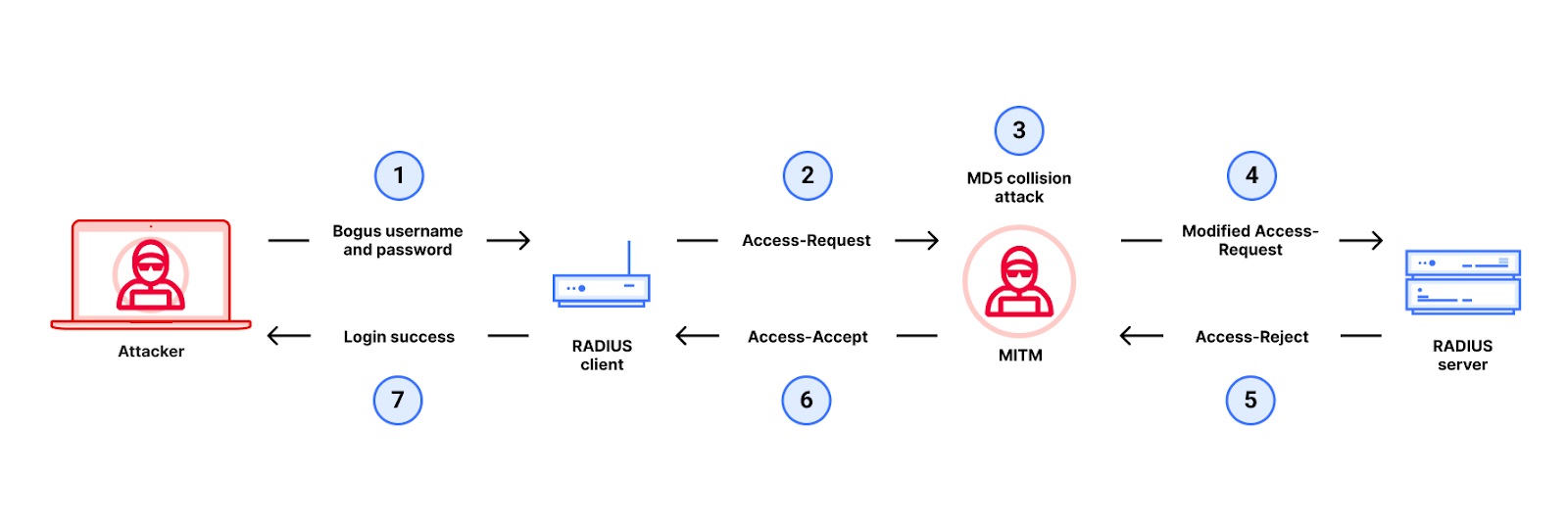
MD5 collision attacks are nothing new. Researchers first busted the hashing algorithm in 2004. Blast-RADIUS is nonetheless a new attack, researchers said in an online FAQ. “While an MD5 hash collision was first demonstrated in 2004, it was not thought to be possible to exploit this in the context of the RADIUS protocol.”
For the attack to succeed, the hacker must calculate a MD5 collision within the client session timeout, where the common defaults are either 30 seconds or 60 seconds. The 60-second default is typically for users that have enabled multifactor authentication. That’s too fast for the researchers, who were able to reduce the compute time down to minutes from hours, but not down to seconds. An attacker working with better hardware or cloud computing resources might do better, they said. They cautioned against ultra-quick client timeouts as a mitigation against Blast-RADIUS, saying that trimming the standard defaults “could be problematic for real users.”
Upgrading the protocol with a newer algorithm such as SHA-2 or SHA-3 isn’t a solution, either. “Such a change would be incompatible with all existing implementations, and thus be equivalent to requiring a new protocol.”
Still, Blast-RADIUS isn’t the second coming of 2014’s Heartbleed bug. System administrators must act, but given the attack’s many prerequisites and costs, Blast-RADIUS is likely only a possibility for nation-states at the moment, said developers of FreeRadius, an open-source RADIUS server.
“In short, don’t panic. Even if you don’t upgrade your NAS equipment, the attack is expensive, and hard to perform,” they said. “You will need to upgrade, but you don’t want to upgrade in a panic, get something wrong, and take your entire network down.”
FreeRadius’ corporate site, InkBridge, provides information for all RADIUS vendors on fixes – which will become part of future versions of the RADIUS protocol. Researchers said the long-term solution is to make an internetwide switch to encrypting RADIUS packets with datagram TLS.
With reporting from Information Security Media Group’s David Perera in Washington, D.C.
