Cybercrime
,
Endpoint Security
,
Fraud Management & Cybercrime
Malicious Script Targets Users in Mexico, Indonesia, Jordan
Why bother building a crypto-locker when Microsoft has perfectly acceptable encryption software preloaded on desktops? Many ransomware hackers agree with that statement – and they’re learning to make such attacks even harder to recover from.
See Also: Guide to Strengthening Mainframe Security
Researchers from cybersecurity firm Kaspersky said Thursday they found a malicious VBScript Microsoft’s BitLocker drive encryption service turned against users in Mexico, Indonesia and Jordan. They dubbed the script ShrinkLocker.
“What is particularly concerning about this case is that BitLocker, originally designed to mitigate the risks of data theft or exposure, has been repurposed by adversaries for malicious ends,” said Cristian Souza, incident response specialist at Kaspersky.
The threat actor behind ShrinkLocker – Kaspersky didn’t make an attribution – isn’t the first to appropriate BitLocker for extortion. But the script goes a step beyond some predecessors by generating a 64-character random encryption key, converting it into a secure string and absconding with the key. The script disables any existing encryption key protectors, effectively blocking recovery options for the victim.
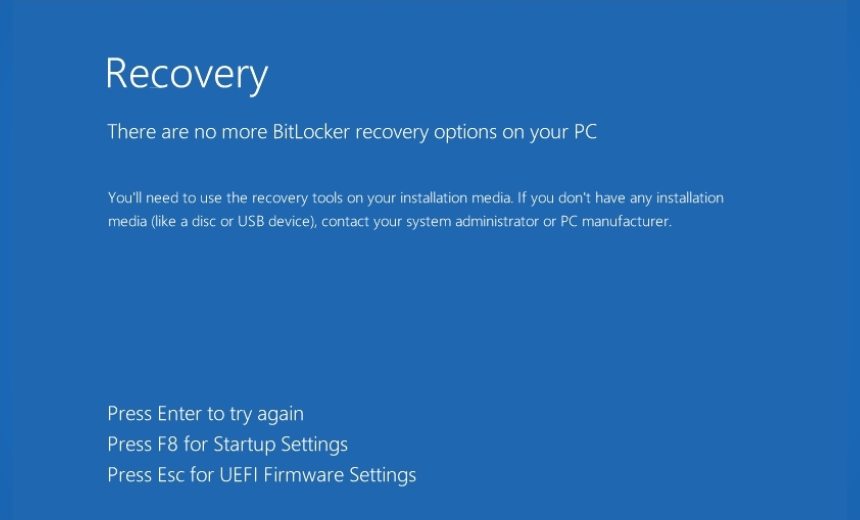
After turning on BitLocker for local storage drives, it performs a forced shutdown. Users who turn the device back on see a blue screen telling them, “There are no more BitLocker recovery options on your PC.”
“The VBS script demonstrates that the malicious actor involved in this attack have an excellent understanding of Windows internals,” the Kaspersky blog post reads.
The malware’s deployment begins with the script, stored as Disk.vbs in the C:ProgramDataMicrosoftWindowsTemplates directory.
ShrinkLocker leverages Windows Management Instrumentation to gather operating system information, checking for compatibility before proceeding with encryption. It specifically avoids older Windows versions, such as XP, 2000, 2003 and Vista.
Once the script verifies the OS version, it performs disk-resizing operations, creating unallocated space to be used for new partitions. It formats the new partitions, forcing the volumes to dismount first, and assigns a file system and a drive letter to each. It uses Windows utilities such as diskpart and bcdboot to manage these processes, ensuring the malware can efficiently encrypt target system drives.
To maximize the ransomware’s impact, ShrinkLocker modifies several registry entries related to BitLocker and system security. These changes allow it to turn on BitLocker even if the device lacks a Trusted Platform Module chip.
ShrinkLocker generates a unique 64-character encryption key for each infected system, using a combination of numerical values, pangram letters and special characters. The key is then converted into a secure string and sent to the attacker via an HTTP POST request.
The POST request contains detailed information about the victim’s machine, including the Windows version, affected drives and the encryption key.
To cover its tracks, the malware clears Windows PowerShell logs, deletes scheduled tasks and forces a system shutdown.
The bulk of the script’s code is not obfuscated, suggesting that attackers had already gained full control of the target system before executing the ransomware.
