Breach Notification
,
Fraud Management & Cybercrime
,
Healthcare
Bipartisan U.S. Senators Demand Change Healthcare Breach Notification by June 21
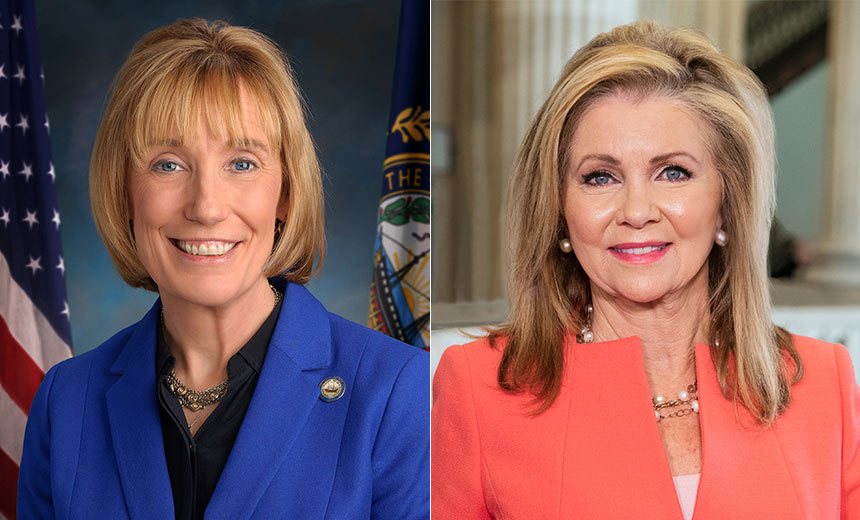
Two U.S. senators are demanding UnitedHealth Group report a breach and notify affected covered organizations and individuals no later than June 21. The bipartisan pair alleges the company is already violating HIPAA by dragging out the notification process in the aftermath of the Feb. 21 cyberattack on Change Healthcare.
See Also: How Enterprise Browsers Enhance Security and Efficiency
More than three months after UHG discovered the ransomware attack, “millions of Americans are still in the dark about the vulnerability of their personal data and health information,” wrote senators Maggie Hassan, N.H, and Marsh Blackburn, R-Tenn., in a letter Friday to UnitedHealth Group CEO Andrew Witty.
“Without urgent action from UHG, patients and providers will continue to be left without any information about the scope of the data breach,” the senators said.
The company has estimated that up to one-third of the American population – or more than 100 million people – might have had their protected health information compromised in the attack by BlackCat, aka AlphV, Russian-speaking ransomware cybercriminals (see: Lawmakers Grill UnitedHealth CEO on Change Healthcare Attack).
The company also admits paying the attackers – who claimed on the dark web to have stolen 4 terabytes of patient data – a $22 million ransom (see: Second Gang Shakes Down UniteHealth Group for Ransom).
UHG “claims to have been undertaking a comprehensive analysis to identify and notify impacted individuals,” the senators’ letter states.
“However, UHG continues to be in violation of HIPAA, which requires covered entities to notify individuals of a known or suspected data breach within 60 days of discovering the breach. UHG must also formally notify impacted business partners, including healthcare providers, in accordance with HIPAA and state law,” the senators write.
Also, to mitigate any confusion among the affected parties, the lawmakers are urging UHG “to assume sole responsibility for all breach notifications by formally notifying OCR, state regulators, Congress, the media, and healthcare providers that it intends to complete all breach notifications on behalf of all HIPAA-covered entities.”
UHG has publicly said it is offering to make notifications and undertake related administrative requirements on behalf of any provider or customer.
On May 31, the Department of Health and Human Services’ Office for Civil Rights refreshed HIPAA guidance first issued in April about the Change Healthcare cyberattack. The updated guidance in the form of frequently asked questions confirmed that affected covered organizations can delegate HIPAA breach notification to UHG, but that they are ultimately on the hook to ensure the notification happens (see: Feds Say Change Healthcare Can Handle Breach Notification).
Neither UHG nor HHS OCR immediately responded to Information Security Media Group’s requests for comment on the senators’ letter, including whether UHG has – or will soon – file a breach report to federal regulators and begin to notify affected covered entities and individuals.
Neither Hassan’s nor Blackburn’s offices immediately responded to ISMG’s requests for additional comment and for whether UHG has responded to their letter.
HIPAA Rules
Some regulatory experts agree with Hassan and Blackburn’s assessment that UHG is already in violation with the HIPAA breach notification rule.
“Per the HIPAA Breach Notification Rule and HHS’ related guidance on ransomware attacks, notifications should have started going out to customers and certain individuals by April 21,” which is 60 days after UHG discovered the Change Healthcare ransomware attack on Feb. 21, said regulatory attorney Sara Goldstein of law firm BakerHostetler.
While UHG might argue that their notification ‘clock’ did not start until they confirmed that the incident involved unauthorized access to PHI, that would be inconsistent with the regulations, guidance and past HIPAA resolution agreements” she said.
Per HHS OCR’s 2016 ransomware guidance, a ransomware attack is considered to be a notifiable breach – meaning the date of discovery is the date the ransomware attack is identified, she explains.
“Under HIPAA, the ‘date of discovery’ is the date a breach is known to the covered entity or, by exercising reasonable diligence would have been known to the covered entity,” she said. “The same goes for business associates. Under HIPAA, notification must be provided to individuals within 60 days of discovery. Therefore, with regard to PHI for which UnitedHealth Group or its Optum or Change Healthcare units are the covered entity clearinghouse, their 60-day clock to notify individuals began the day that they identified the ransomware attack, Goldstein said.
